Vendor onboarding is the vital first step in your vendor risk management strategy. Using Protecht’s vendor risk management (VRM) solution, you can digitise complex, data-heavy manual processes to drive a more efficient and seamless onboarding. In this blog, we will consider the five key stages of vendor onboarding using Protecht ERM.
The process of onboarding runs all the way from initial identification of vendors to the signing of contracts. Following the steps below in a structured way will ensure that you remain on top of the process throughout:
- Identification of your vendors
- Initial tiering
- Initial due diligence
- Go/no-go decision
- Onboarding and contracting
Subscribe to our Knowledge Hub to make sure you catch the rest of our Vendor Risk Management blog series:
Identification of your vendors
The first step in the vendor risk management process is to identify all vendors that your organisation engages with. It is essential to maintain an accurate and up-to-date repository of all vendors to ensure that your organisation can effectively manage its risks.
Protecht offers an efficient way to capture all relevant vendor information using the Vendor's Business Details record. This tool is designed to track vendor-specific data, giving your organisation a clear overview of who your potential vendors are. It's your starting point in managing and mitigating vendor-related risk, as it ensures all necessary vendor details are captured right from the beginning.
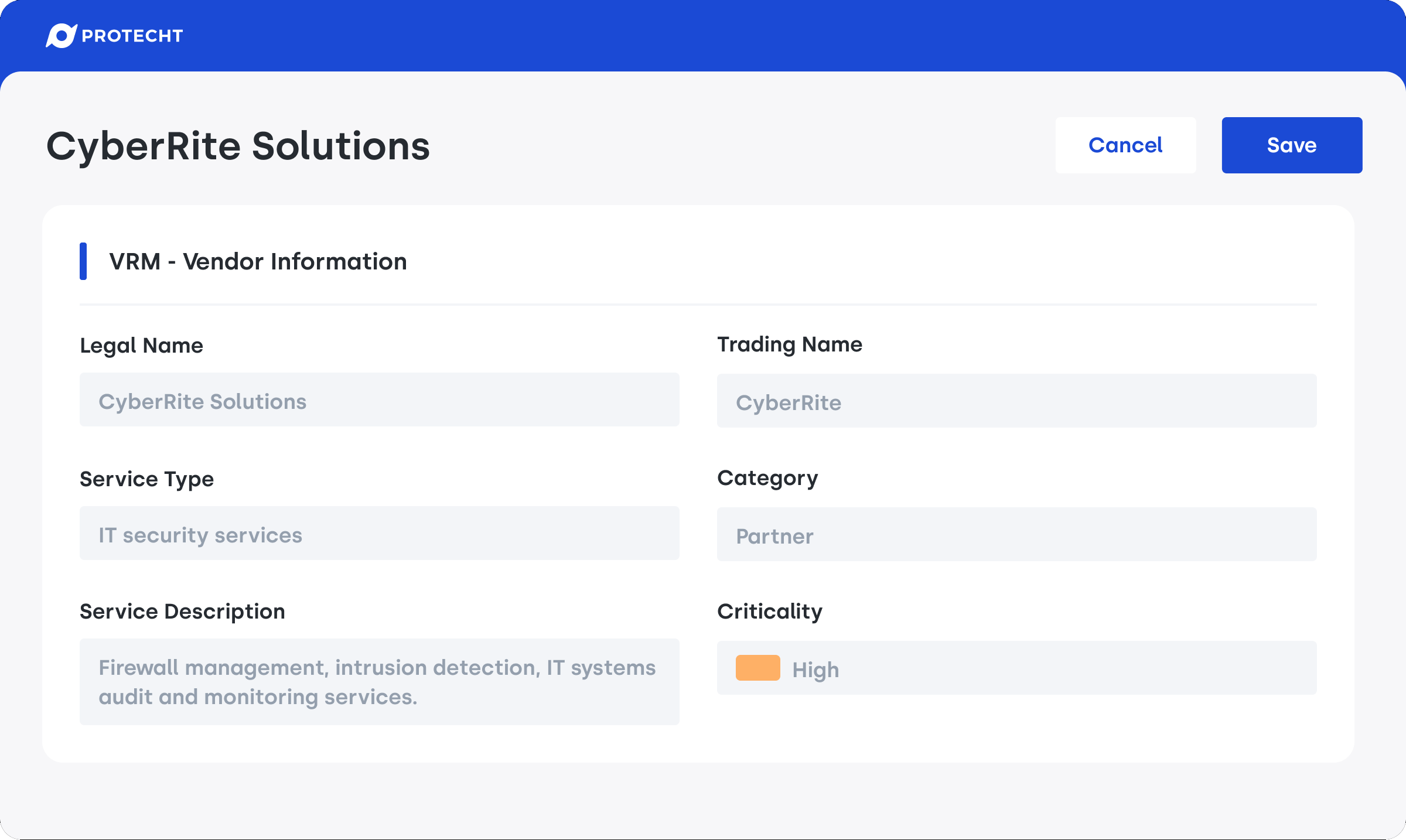
Vendor's business details record in Protecht ERM
Initial tiering
Managing all vendors in the same way is not practical. Comprehensive due diligence that is burdensome for low-risk relationships adds little value. An initial tiering of vendors based on pre-defined criteria enables appropriate attention and resources are allocated throughout the vendor lifecycle.
The solution also supports consistent tiering with internal questionnaires to determine inherent risk, so that different members of your team consider the same criteria when evaluating vendors.
Protecht’s VRM solution enables you to define and assign tier levels to your vendors using various metrics such as spend, potential risk, and criticality. The tiering process is a crucial step as it helps prioritise vendors for further due diligence and risk assessment.
Key questions to consider at this point include:
- Strategic importance – Is this vendor critical to our organisational success, or are they a low impact third-party?
- Business continuity – How would disruption of this vendor affect our operations?
- Information security – Are we sharing confidential or customer data with this vendor? Do they have access to any of our systems?
- Compliance – Will this vendor be managing or otherwise assisting us with our regulatory or compliance obligations?
- Financial – What is the value of this engagement?
- Reputational – Will this engagement be highly visible to the public? If the vendors reputation is impacted, would we also be affected by association?
By assigning vendors to specific tiers, you can prioritise which vendors require the appropriate level of due diligence and monitoring. This can save time and resources by allowing you to focus on higher-risk vendors first.
Initial due diligence
The initial tiering process helps inform the types and extent of due diligence to be conducted. You might have lower information security standards or assurance thresholds for low tier vendors who have no access to your systems or customer data. Conversely you might require substantial assurance over business continuity arrangements, such as evidence of testing, for vendors that support your critical operations or important business services.
Conducting this due diligence usually involves issuing vendors with tailored questionnaires from a standard library to enable a consistent approach.
Protecht's VRM solution allows you to streamline this process through its integrated Questionnaire tool to easily assign assessments to your vendors. This tool comes with a library of ready-to-use industry-standard assessment questionnaires like Standardized Information Gathering (SIG) Lite and SIG Core from Shared Assessments, as well as the option to create custom questionnaires:
- SIG Lite is typically used for lower risk vendors, or as a preliminary assessment
- SIG Core is typically used to assess vendors storing or managing highly sensitive or regulated information, or who are critical to your business
- The risk domains covered by the SIG questionnaires cover governance and risk management, information protection, IT operations and business resilience, and security incident and threat management
This automated and streamlined approach makes the vendor due diligence process easier and more efficient.
Go/no-go decision
Based on the initial due diligence results, your organisation needs to make a go/no-go decision. This decision is crucial and needs to be based on comprehensive data.
Initial due diligence shouldn’t be a tick the box exercise – it is intended to inform a decision on whether to proceed or not. This decision should be based on analysis of the data you’ve collected from the vendor, and whether it exposes your organisation to risk that may be outside of your appetite.
Protecht supports this decision-making process by allowing you to assess Vendor Questionnaires, with ability to score and rate questionnaire and record and remediate any findings and issues, as well as leverage risk assessments to set the rating against vendor risk categories.
Onboarding and contracting
Once the vendor has the green light, there is the formal process of contracting and onboarding. While it is likely to have already been addressed when discussing the initial business case with the vendor, now is the time to ensure clear expectations have been set regarding service level agreements, contractual obligations, and requirements regarding ongoing assurance activities.
Protecht simplifies this process with its contract management feature, allowing you to capture pertinent contract details, track renewals, and send reminders to contract owners when contracts are due for renewal.
After the vendor is onboarded, Protecht aids in ongoing vendor monitoring with features like Monitoring and Review where you can keep a record of past and scheduled periodic tasks, as well as automatically scheduling periodic due diligence questionnaires and periodic risk re-assessments.
Protecht’s VRM solution also includes pre-designed analytic dashboards to track the health of the entire vendor portfolio, providing insights on vendor management, risks, questionnaires and findings and issues.
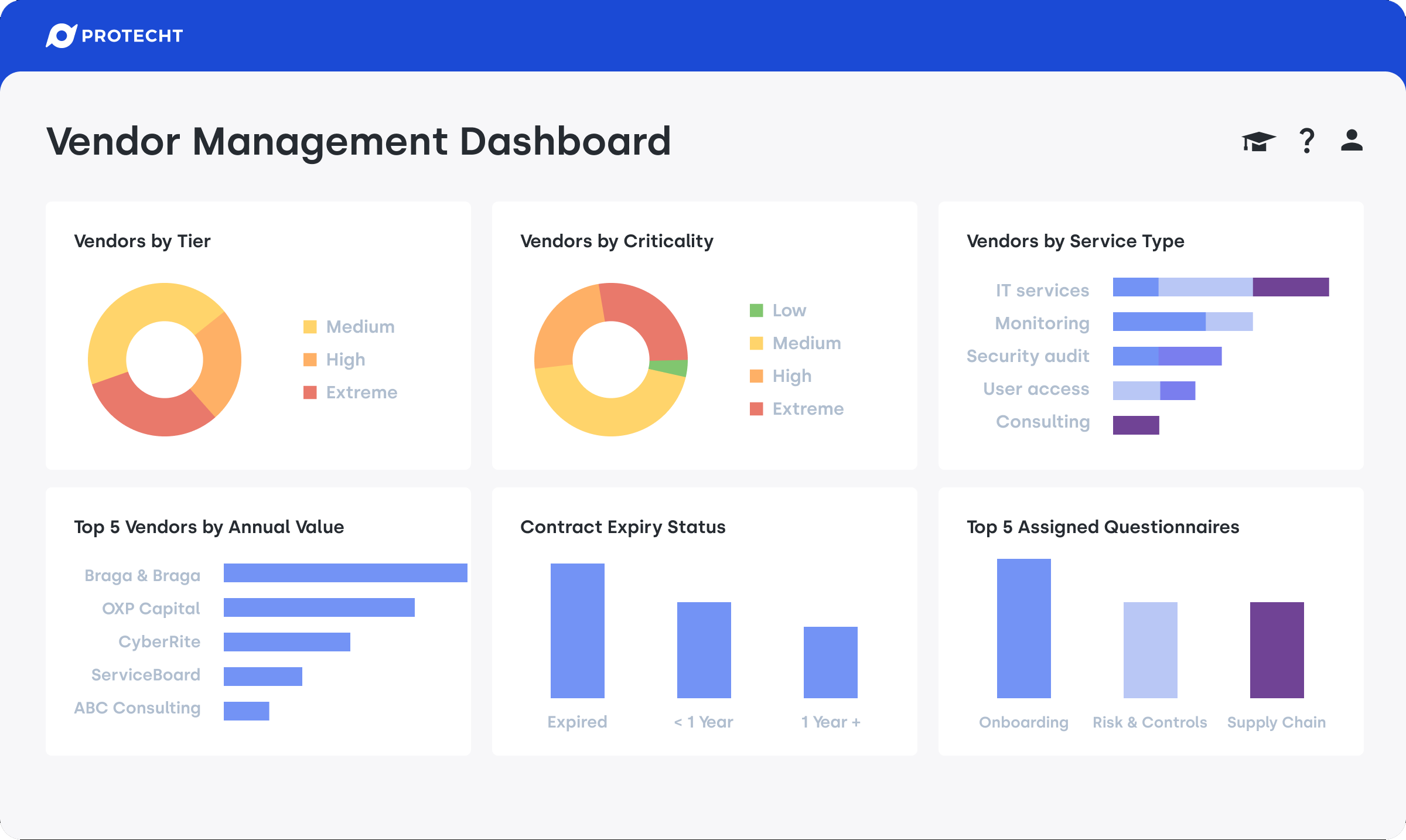
Vendor management dashboard in Protecht ERM
Conclusions and next steps
Vendor onboarding is a crucial aspect of vendor risk management. An efficient onboarding process reduces the risk associated with new vendors and sets the stage for a strong, mutually beneficial relationship. With Protecht, you can leverage the power of automation to streamline your vendor onboarding process, facilitating efficiency and risk mitigation.
If you want to know more about your vendor risk, download our Vendor Risk Management eBook for a detailed step-by-step guide of to build an effective vendor risk management program.
Subscribe to our Knowledge Hub to make sure you catch the rest of our Vendor Risk Management blog series:

