Protecht held a webinar on APRA’s draft Prudential Standard CPS 230: Operational Risk Management earlier this month. The attendees completed several polls and asked a range of questions, some which we were able to answer during the webinar and others not. This blog contains a summary of all the poll results, plus the questions asked in the webinar and our responses.
Register here to watch the recorded webinar
CPS 230 webinar poll results
Which best describes your organisation or those you work with?
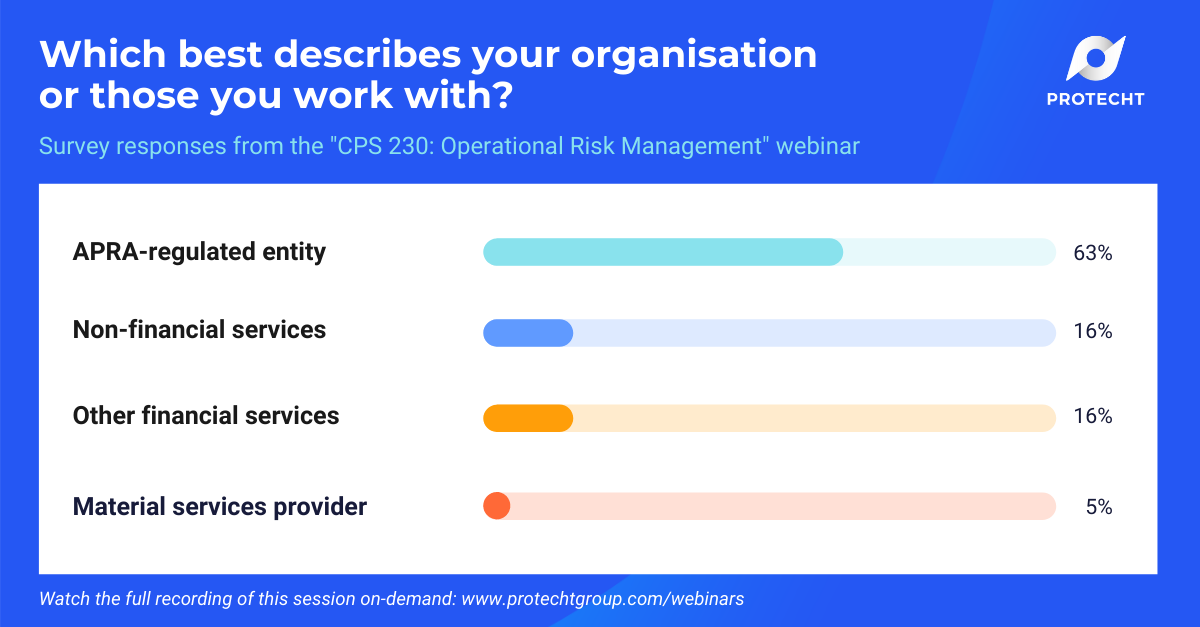
It’s not surprising that APRA-regulated entities made up the lion’s share of our attendees. What is great to see is other people in financial services joining us – it will be interesting to see if ASIC adopts some of these approaches in the next few years for financial service providers that it regulates. Also great to see those outside of financial services, identifying emerging expectations that might flow into other sectors, or simply looking for good practice they might adopt. I think it is safe to say that entities adopting operational risk practices aligned with CPS 230 can do so with a ‘no regrets’ approach even if they aren’t regulated by APRA.
To what degree do you believe business line management has taken responsibility for risk management in your organisation?
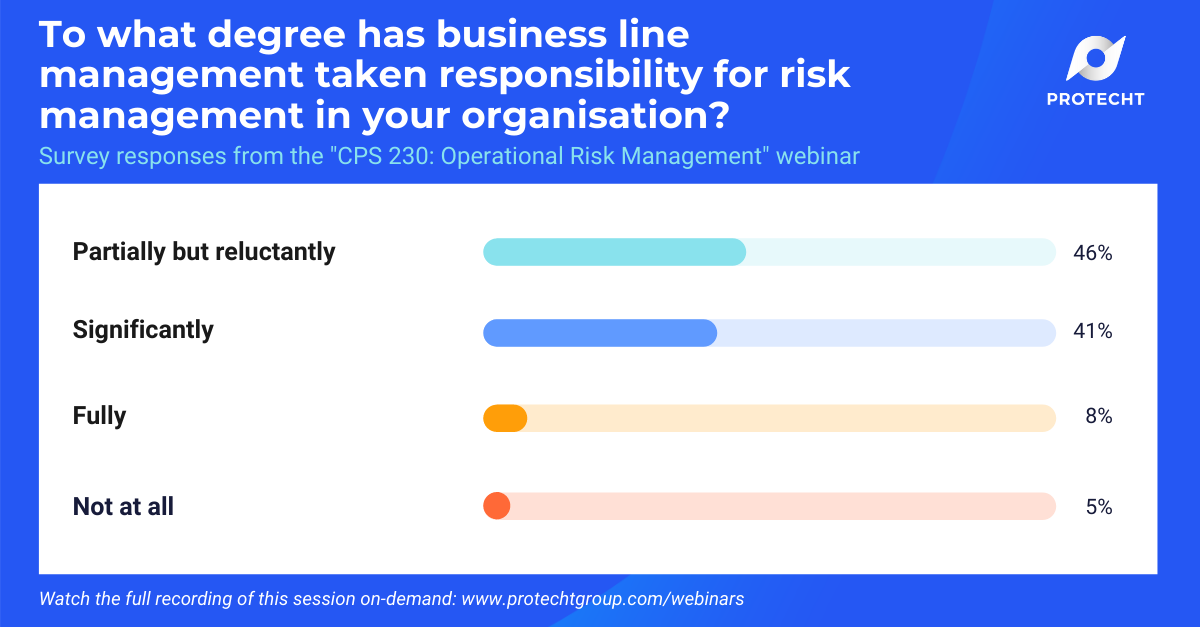
You will hear us say at Protecht that everybody is a risk manager! The fact that just over half of the responses were only partially or not taking responsibility for risk management is telling. Clearly there is still work to be done on the value proposition to the organisation (and more specifically its people) of effective risk management.
To the 8% where risk management responsibility is fully embedded, excellent!
To what degree does your current risk management deliver an integrated risk profile?
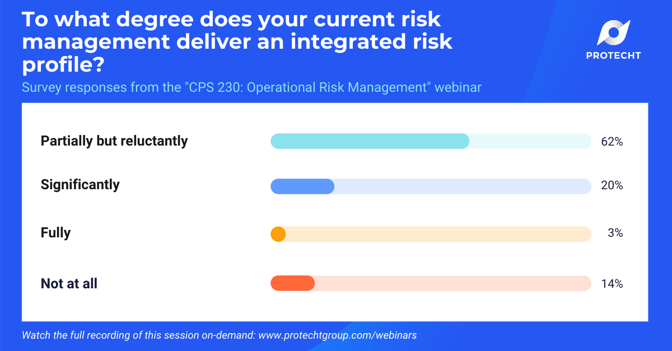
With partially or not at all approaching 80% of all responses, clearly there is lots of room for improvement! CPS 230 focuses on the interdependencies between various elements of operational risk management, which we also see expanding into other types of risks. One of our goals at Protecht is to help organisations break down silos, take an enterprise approach to managing risk, and provide relevant information to decision makers at the time they need it.
CPS 230 questions and answers
Do you think operational risk teams in the future will include BCP and vendor management?
What is the perspective around governance and BCMS documentation with reference to policy?
Does the standard require credible BCPs, and how are they defined if so?
Is going further than fourth party suppliers going to be a challenge?
Do TPRM requirements extend also to renewals of contracts?
How are related parties covered within third party risks?
Do you expect a compliance grace period with regards to contracts including the access clauses?
What is the difference between MAO and RTO?
Do you include supply chain in your list of disruption?
Any thoughts on assessment of compliance costs?
Will APRA withdraw the existing standards CPS 231 and CPS 232?
Do you think operational risk teams in the future will include BCP and vendor management?
While the draft standard outlines requirements for effective risk management practices, including across business continuity and vendor management, it doesn’t outline where day-to-day responsibilities must or even should sit. The Boards accountability is defining the roles and responsibilities of Senior Management for performance of these activities.
In some organisations we work with, people responsible for business continuity and vendor management frameworks and processes do form part of operational or enterprise risk teams. In some smaller regulated entities, a single role may perform all of these functions. We anticipate that at the very least all should be working very closely together as part of an enterprise risk management program.
If you have specific causes, risks and controls, it becomes difficult to reuse them – but if you aren’t specific, it’s difficult to capture the risk causes and controls appropriately. What's your thoughts on this in terms of linking risks, incidents, etc?
We find the use of taxonomies, which may have multiple levels or granularity, work best. In practice when documenting and responding to incidents, this allows for accurate documentation of the specific causes and the ‘risk story’, while allowing for aggregated reporting. The different levels in your taxonomy allow you to report at different levels.
Doesn’t the standard just look like a good BCM and BCP: processes, resources, scenarios, risk, resilience/recovery, etc?
We are sure that this will be open for debate for some time. What is clear is the BCM and BCP form a major part of Operational Resilience. We see Operational Resilience as bringing together all of the elements which impact resilience such as BCM/BCP, Third Party Risk Management, Cyber Risk Management and so on, into one consolidated view linked via the identified critical operations and enhanced by some additional functionality and reporting. Protecht’s Operational Resilience solution takes this approach.
What is the perspective around governance and BCMS documentation with reference to policy?
Perhaps of note is that the draft standard requires a service provider management policy, but does not require a specific business continuity management policy / framework (beyond maintaining a credible business continuity plan as part of its risk management framework). CPS 232 (the existing business continuity prudential standard in effect until 31st December 2023) does state that the Board must approve the BCM policy, so this requirement is currently in effect. Other guidance on business continuity, such as ISO 22301, recommend policies approved by the top governing body.
The Board is responsible for allocating roles and responsibilities to Senior Management in relation to business continuity, and the Board must approve the Business Continuity Plans. We would expect in practice that there is a Business Continuity Policy or Framework that is owned by the assigned Senior Manager role. We anticipate that role (or teams within that business line) would maintain oversight of business continuity documentation across the organisation to ensure a consistent approach. This could be part of a broader Operational Resilience policy or framework.
Does the standard require credible BCPs, and how are they defined if so?
Based on the draft standard there is limited information on APRA’s expectation on how to measure the effectiveness of the business continuity plan. If the question is what makes for a credible business continuity plan; one that increases the likelihood and speed with which you will be able to continue and recover your operations at the most efficient cost!
Would you expect ‘payments’ as a critical operation would include payroll as well as accounts payable activities under the standard?
No, on the basis that critical operations are defined by material adverse impact on its depositors, policyholders, beneficiaries or other customers, or its role in the financial system. We believe that APRA’s inclusion of payments as a critical operation relates to customers being able to make payments (purchase at merchants, make online payments and transfers etc). While functions like payroll and accounts payable are highly unlikely to meet these definitions, you may still choose to have business continuity plans that consider those functions. They just won’t form part of your critical operations for CPS 230 purposes. It might however make sense to use the same methodology and processes to include payroll aimed at keeping your most valuable resource, your people, happy!
Is going further than fourth party suppliers going to be a challenge?
Yes, it would be! The standard requires the service provider management policy to set out the entities approach to managing risks associated with fourth parties that their material service providers rely on. It may be noteworthy that this requirement appears to only apply to fourth parties of material service providers, implying it is not required for other service providers. This is, unless “fourth parties” include 4th, 5th, 6th and so on!
As worded, the standard does not appear to require looking beyond fourth parties. It also doesn’t provide any guidance or expectations on what an entities approach should be to managing risks associated with fourth parties; only that they have one in their policy. Given its inclusion in the standard, we would expect that it has to be more than simply documenting a list of the fourth parties. We anticipate this will be further articulated in future guidance.
Do TPRM requirements extend also to renewals of contracts?
Yes, section 52 of the draft standard outlines due diligence requirements for material service provider agreements, including when entering, renewing, or modifying an arrangement. Section 53 and 54 include specific requirements that must be included in a legally binding agreement. Read in isolation, these two sections appear to be ‘always on’ and don’t refer to renewals. However, APRA have included in their discussion paper a question regarding transitional arrangements, indicating there will be some grace period. Hopefully your contract renewal periods will be within the implemented transition period.
How are related parties covered within third party risks?
You rightly point out that today one entity in a group may provide services to other related parties in that group. This is noted by the draft standard at section 48, supported by footnote 14. There is a requirement to keep a register of material service providers, which does include related parties. There are no exclusion clauses or concessions for related parties. The implication is that you will need to follow the requirements of the standard, including formal agreements with the minimum required clauses, and follow monitoring and review requirements.
Would providers such as Microsoft who provide commodity type services such as email be classified as material?
The key question in determining whether they are a material service provider is whether you rely on the service provided to undertake a critical operation. Given the list of services listed by APRA in the draft standard and the requirements to be included in contracts, we expect the bar to be relatively high on who needs to be considered a material service provider. At face value email on its own is unlikely to underpin critical operations or fall within the definition of ‘core technology services’, though this may depend on your specific operations.
Do you expect a compliance grace period with regards to contracts including the access clauses?
APRA have included eight questions in their discussion paper during consultation, and one of those questions is about transitional arrangements:
“What form of transition arrangements and timeframe would be needed to renegotiate contracts with existing service providers (if required)?”
So we would anticipate that there will be a grace period that will be communicated after the consultation period.
What is the difference between MAO and RTO?
At Protecht we recommend using Maximum Allowable / Acceptable Outage (MAO) at the operations or business services level. This is the longest period of time that the business operation or service could fail before it causes intolerable harm to the achievement of organisational objectives.
Recovery Time Objective is the time at which you would like to cover those operations, which would be less than the Maximum Allowable Outage. Recovery Time Objectives can similarly be applied to individual resources required to support the operation or business service. Given the many-to-many relationships that can occur between resources and multiple business operations, the RTO at the resource level should be equal to or less than the shortest RTO of any one of the associated business operations. Building these relationships allows you to see:
- For an RTO of an individual operation, whether the RTO of each required resource is within that timeframe
- For the RTO of each resource, whether it is less than each associated RTO of the business operations it supports
Protecht have built our Operational Resilience module to support these many-to-many relationships. We have purposefully left out the word ‘critical’ in this explanation, as there may be other operations that are important to your organisational objectives beyond APRA’s definition that you may want to consider in your business continuity planning.
For critical operations, the MAO may be the same as the tolerance level timeframe as required by APRA; however there may be instances where your MAO may be lower than the defined tolerance level. An example may be where the financial impact to the organisation is severe before it has significant impact on customers.
Do the updated BCM requirements and the pivoting of the focus to critical operations constrain the scope compared to current BCM?
Only if you let it! There is nothing that prevents you from developing BCP capability beyond the specific requirements of APRA. We recommend including other operations in your business continuity program beyond APRA’s definitions if disruption would impact on your ability to achieve your organisational objectives.
Is there any requirement for uplift of disaster recovery capabilities? Is 'materiality' defined in this context?
There is a requirement to maintain a credible BCP that includes Disaster Recovery Planning for critical information assets. We recommend that these are linked but separate documents and processes. The draft standard mentions materiality in respect of critical operations, not disaster recovery specifically. The inference is that disaster recovery capability should be sufficient to support business continuity plans and recovery of critical operations (as a minimum) within the defined tolerance levels (which may include both time and data).
Does the proposed standard downgrade the importance and special attention required for BCM? How does this align to ISO22301 and ISO31000?
My view has always been that business continuity is an integral part of risk management. From an enterprise risk management perspective, the disruptive events are risks, and business continuity plans are reactive controls. Preventive controls are applied to potential causes where applicable (aligned with APRA’s reinforced message to reduce likelihood of disruption). Business continuity processes are simply given extra attention due to the potentially high impact of the identified risks.
As the standards (APRA’s and ISO’s), are principles-based there is no misalignment between them. APRA do have a focus on harm to consumer and financial stability, while ISO31000 and risk management more generally is (or should be) about organisational objectives. To that end, we recommend focusing on your organisational objectives and the associated risks first, which we would expect covers most of APRA’s expectations.
On ISO22301, we don’t believe there is misalignment. However, APRA requirements may require you to capture or consider some information not captured today in your business continuity management program, particularly the three different types of impact tolerances required.
Is there a requirement to amalgamate operational risk framework documentation with business continuity frameworks?
There is no requirement to do so, but if you can simplify while providing sufficient direction and allocation of responsibility, we recommend you do so. If you have multiple policies or frameworks, we recommend they reference each other where applicable to show how they interrelate.
Can you provide some guidance on defining the tolerance levels APRA constantly talks about? It doesn't sound like the traditional BIA timeframes are suitable?
On the first point, we anticipate providing further guidance, such as webinars and blogs, as more information from APRA develops. Protecht will also provide consulting services to organisations seeking to establish their tolerance levels.
On the second point, it may depend on what you mean by ‘traditional’ BIA timeframes, and the assessment criteria that were used in those BIAs. Some organisations will assess these based on impact to the customer (aligned to APRA’s definition), and the tolerance level may be the same as a more ‘traditional’ Maximum Allowable Outage. If they have only been assessed based on the financial impact to the organisation (as one example), there may a difference.
Do you include supply chain in your list of disruption?
While we called out being indirectly affected by third parties who have experienced disruption in the webinar, we didn’t call out supply chain directly. You’ve highlighted a good point; someone in the supply chain could simply ‘fail’ due to poor internal management (dare we say, due to poor operational risk management), not just external disruptions.
How do you view assessment of end-to-end operations from the lens of customer journey in contrast to an end-to-end view of an entity’s products and services?
I think this comes down to how you define the customer journey vs products and services. In my experience with customer journeys, they consider the whole lifecycle of the customer through the customers eyes, and how they feel during their journey.
The customer journey for a house insurance policy might include:
- Need to obtain insurance identified
- Initial discovery / investigation of policy inclusions and requirements
- Obtain quote from multiple insurers
- Choose and purchase insurance
- Make an insurance claim during the life of the policy
- Sell the house and cancel the policy
- Continue to advocate for the insurer due to their high level of service
I would expect most customer journey maps to delve deeper into each step, but in this example, some of the customers journey is outside of the provision of products and services of the insurer. At least one specific step, making a claim, would be considered a critical operation by APRA that would require inclusion in a business continuity plan. This is a service with a particular outcome that, if disrupted for a period of time, would cause intolerable harm to customers.
Any thoughts on assessment of compliance costs?
My initial response is to not only consider the cost of compliance, but the benefit of compliance! Organisations should consider good risk management as an enabler of sustained performance and to improve the likelihood of achieving objectives (and avoiding catastrophic failure) before considering it a compliance exercise.
With that aside, there are two main costs to consider; the cost of change, and the cost of ongoing compliance. A high-level plan:
- Identify current practice (including any deficiencies)
- Design proposed practice
- Conduct a gap analysis between current practice and proposed practice
- Identify cost to change current practice (training, uplift and implementation)
- Identify ongoing cost of compliance, such as human capital and service providers to support new or changed requirements
We appreciate that is high level, and each organisation will need to delve into different specifics. We anticipate this will come into sharper focus once APRA releases additional guidance; however some may need to start petitioning for the required resources before then which can make the assessment challenging.
Circling back to the first point, if at all practical present it with a return on investment, not just a cost.
Will APRA withdraw the existing standards CPS 231 and CPS 232?
Yes, they will be replaced by CPS 230. Based on current information, CPS 231 and CPS 232 will remain in effect until 31st December 2023 before CPS 230 comes into effect 1st January 2024.
What is the ‘right’ level of granularity for end-to-end view of risks and controls, and what is a ‘plausible’ scenario?
We agree this will be a challenge, and there won’t be a one size fits all. We recommend two types of scenarios; resource-based scenarios, and event-based scenarios. Resource-based scenarios assume one resource (or combination or resources) are unavailable, and assess the effect on critical operations. This may then be used to prioritize preventive or reactive controls applied to specific resources which have the highest impact on the organisation if they fail.
Event-based scenarios consider scenarios based on particular threats or events, and then assess which resources are likely to be unavailable or affected. The benefit of this approach is that it may allow for increased ability to assess the likelihood of particular events, and consider collective controls or particular business continuity responses to address a range of scenarios. With a requirement for scenarios to be ‘severe but plausible’ it may require some imagination and collaboration of different teams and skillsets, particularly to ensure they are sufficiently severe.
Next steps for your organisation
Protecht recently launched the Protecht.ERM Operational Resilience module, which helps you identify and manage potential disruption so you can provide the critical services your customers and community rely on.
Find out more about operational resilience and how Protecht.ERM can help:
- Watch our CPS 230 webinar
- Watch our operational resilience webinar
- Download our operational resilience eBook
- Find out more about our Operational Resilience module
