The deferral of the start date for CPS 230 by 18 months indicates the amount of work required to comply. This extra 18 months is not a time to relax, but a time to prepare. The extent of work required is substantial as the standard is demanding a major uplift to operational risk management frameworks and processes.
In our recent thought leadership webinar, Protecht’s Chief Research & Content Officer David Tattam and Research & Content Lead Michael Howell reviewed the requirements of CPS 230 and explored how you need to prepare to meet the requirements of the standard. This blog discusses the audience polls and the questions asked at the webinar.
If you missed the webinar live, then you can view it on demand here:
Poll results
How integrated is your operational risk management, business continuity, and third-party risk management?
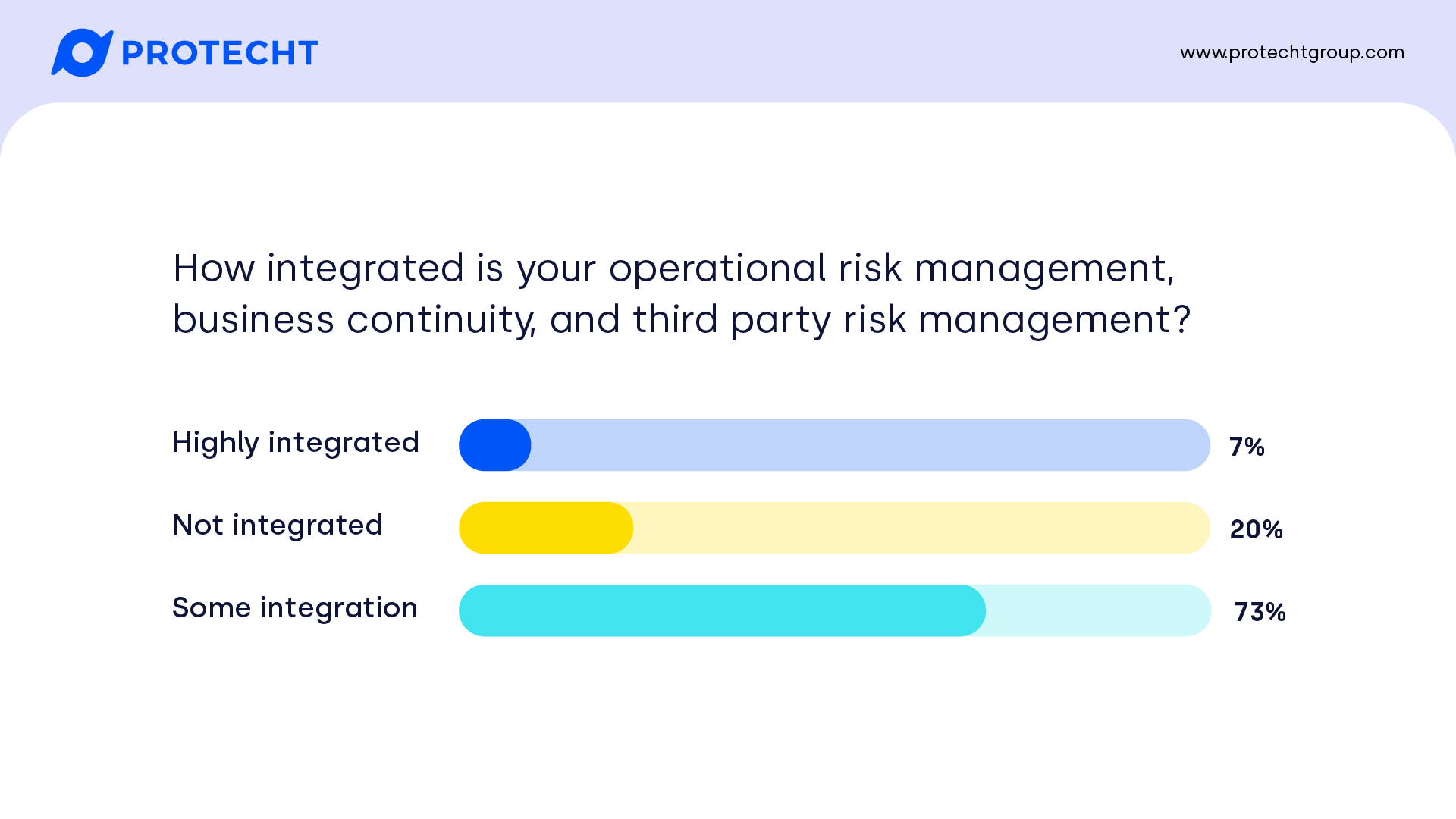
APRA are expecting a more integrated approach to managing operational risk, including the integration between ‘traditional’ operational risk management, business continuity and third-party risk management (those latter two are just specific types of operational risk). That integration can be hard to achieve, especially without effective tools – demonstrated by only 7% of our participants considering themselves highly integrated.
On the plus side, almost three quarters have at least some level of integration. We anticipate that for most this will continue to be a journey right up to the deadline for CPS 230 implementation. The biggest challenge is having a single source of truth, consolidation of information that might be currently captured in siloes, and ensuring everyone has the data they need while that consolidation is taking place.
Questions
Could you consolidate some payment types when considering critical operations – for example, VISA, EFTPOS, direct debit cards?
Given the smaller size of our entity, are process mapping requirements a must?
What is the process level (1, 2 or 3) required to meet the requirements of CPS230?
Should organisations be prioritising the mapping of critical operations only, or all end-to-end processes and value streams?
Is there a roadmap to identifying critical operations?
Do you think APRA will apply the same approach as CPS 234 and confirm compliance through tripartite arrangements?
How should we go about defining material service providers?
Is there guidance from APRA for entities who might be considered a material provider to an APRA entity?
What steps and actions should tech service providers be doing in preparation for the implementation of CPS230?
What are the differences and overlap between critical operations and material service arrangements?
For non-APR-regulated entities, how do you view other regulators’ attitudes towards the requirements of CPS 230?
We use the risk management and vendor management modules in Protecht. Does the operational resilience module integrate with these to ensure data is not duplicated?
Could you consolidate some payment types when considering critical operations – for example, VISA, EFTPOS, direct debit cards?
At face value, those payment types appear to be similar, but it comes down to what is practical, and the similarities and differences between them in your organisation. Let’s take one step forward – after identifying your critical operations, you will need to determine the tolerance levels. This will usually be driven by the customer demographic or external factor that will be most impacted.
If the impact from disruption would be the same across all payment types (such that their tolerance levels would be identical) then it makes more sense to consolidate. However, if they are all different, then consolidating would mean the lowest tolerance level applying to that whole group. Especially if the resources required to support those operations differ, this might require faster recovery times or more comprehensive business continuity plans (and associated costs) than are required.
Given the smaller size of our entity, are process mapping requirements a must?
APRA have not said explicitly that you must map your processes. However, they have dropped plenty of hints that it is expected. Section 27(b) of the finalised standard requires APRA regulated entities to:
Identify and document the processes and resources needed to deliver critical operations, including people, technology, information, facilities and service providers, the interdependencies across them, and the associated risks, obligations, key data and controls.
On top of these requirements to map independencies and associations, Senior Managers are responsible for ‘end-to-end’ processes – a phrase they also use consistently in the CPG guidance. We interpret APRA’s message as: if you don’t understand your processes, how can you understand the risks to those processes? To take that a step further, if APRA become aware of a control failure or incident in your organisation, how will you respond to questions about how you’ve understood your end-to-end processes sufficiently well in order to mitigate those incidents or failures?
What is the process level (1, 2 or 3) required to meet the requirements of CPS230?
We expect that for most organisations starting out on the process mapping journey, that you keep it at the highest level. Consider the high-level critical operation, and the core processes that are needed to deliver it. For the requirements of CPS230, if you are getting down to work instruction level, you are going too far.
Some organisations may already have more mature process mapping, and already have multiple levels defined for their process mapping. If you do, you should of course leverage these.
Should organisations be prioritising the mapping of critical operations only, or all end-to-end processes and value streams?
The short answer is that you should prioritise mapping of critical operations. However, I would suggest that mapping all your operations provides more detailed information to support broader operational risk management and allocation of resources. Many of the resources and processes required to deliver your critical operations will also support other operations. Assessing the aggregate impact of disruptions to resources – which can include important internal services not contemplated by the definition of critical operations – enables improved decision making.
Is there a roadmap to identifying critical operations?
We'll expand slightly here on a point that we made in the webinar.
David started with developing a stakeholder map. The only way to understand the risks you bring to your stakeholders is to understand who they are. Once you have understood your stakeholders, you can start to identify the operations that, if disrupted, would cause them harm.
To expand on that, consider the products that you have or provide to those external stakeholders. Products by themselves are not critical operations, but are the source of value for your stakeholders. Finally, consider how your customers use those products. This gets close to the heart of critical operations – the final outcomes that you deliver to your stakeholders. Where applicable, consider Target Market Determinations to assist in this process.
While we’ve used the term ‘stakeholder’, shift the lens where applicable to the impact on broader financial stability.
Do you think APRA will apply the same approach as CPS 234 and confirm compliance through tripartite arrangements?
APRA have been clear that they will be assessing regulated entities’ readiness early 2024, that critical operations and material service providers should be identified by mid-2024, and tolerance levels defined by the end of 2024.
Beyond the standard actually coming into force, it is too early to tell if they will take the tripartite approach. Given some recent communication from APRA – such as this speech by Therese McCarthy Hockey – we expect that APRA will be looking to enforce the standard more heavily and earlier after it comes into force.
How should we go about defining material service providers?
Let’s start by going straight to the source, and quote paragraph 94 of the draft guidance:
94. In determining which service providers are material, an entity would consider:
a) whether the service supports a critical business operation;
b) the totality of services provided by the service provider;
c) the nature of the services provided and whether it exposes the entity to material operational risk, including for example cyber risks or mis-selling risks, or in the event the service or service provider is compromised (operationally, financially or reputationally);
d) the degree of difficulty in exiting the arrangement and transitioning delivery of services to another service provider or bringing it in-house; and
e) whether the service involves sensitive or critical information assets, as classified by the entity for the purposes of CPS 234, including for example the consequence of a data breach.
APRA have commented that they expect entities to have identified critical operations and material services providers by mid-2024. My initial suggestion would be to align identification of your material service providers with process mapping – which helps with sub-paragraph a).
In the absence of process mapping, you likely already have some data that provides insight to which might be material service providers. Two likely sources:
- Contract registers or vendor registers that include an assessment of importance (and ideally why it is important)
- Business Impact Analysis or other BCP artifacts that identify important resources owned by vendors
Note that these pre-existing sources may not be aligned directly with critical operations, so will have to be reviewed in that light.
A common assurance activity is to compare finance records against contract registers or vendor management systems, to validate that service providers have not been missed during other identification processes.
To sum up:
- Start top down from critical operations, resources to deliver, and the service providers required to deliver them
- Validate using bottom up, reviewing lists of service providers to ensure they are mapped appropriately to critical operations
Is there guidance from APRA for entities who might be considered a material provider to an APRA entity?
APRA defines them in paragraphs 49 and 50. Even if services do not fall under the services listed in paragraph 50, you still need to consider the general requirements of paragraph 49 – whether the services provided are relied upon in order to deliver a critical operation. This means that in some circumstances, the same service may be material to one regulated entity, but not another.
If you provide services to an APRA-regulated entity, the following questions can help guide whether you will be considered material:
- For the services I provide, what operations of the APRA regulated entity do they support?
- Would disruption to the service I provide significantly impact the regulated entity, in particular flowing on to its external stakeholders?
- Beyond disruption, does the provision of my services bring significant operational risk to the entity?
What steps and actions should tech service providers be doing in preparation for the implementation of CPS230?
Proactivity by potential material service providers can become a competitive advantage. If you haven’t already, review the material service provider requirements of the standard and guidance. What we expect to see is that many of the requirements will be pushed on to the material service providers through contracts and service level agreements (some clauses will be required directly by the standard). Here are some of the key preparatory actions:
- Have an effective operational risk management program in place that can be evidenced (this should go beyond cyber)
- Have an effective process for controls management, in particular ensuring sufficient documentation for controls assurance and testing that can be provided to regulated entities. This can include independent assurance
- Have a business continuity program that is more than a piece of paper; you should be able to demonstrate it has been tested and is effective – especially related to the services that you are providing to the regulated entity
- Conduct process mapping of internal processes that support delivery of your services; this will help demonstrate to your customers that you understand your own resilience capabilities
- Adopt a service provider policy (aligned with CPS 230) to provide assurance to APRA regulated entities over how their fourth parties are managed.
Where applicable, review your capability and capacity to ensure you can meet those requirements. The earlier you can go out to market and say that you are ‘CPS 230 ready’, the more competitive you will be.
One final thought – review the specific requirements of paragraphs 54 and 55 of the standard, which covers minimum contract clauses. To the extent required, socialise these requirements internally to verify your organisations appetite for these requirements, how they might be addressed or met, and make any changes required to prepare.
What are the differences and overlap between critical operations and material service arrangements?
There is not a one-to-one relationship, but there is an overlap. Firstly, a notable update between the draft and final standard is the distinction between a material service provider and material service arrangements. You may have multiple arrangements with a service provider, but not all will be material. A material service provider is any service provider with one or more material arrangements.
To look at the difference between critical operations and material service arrangements, let’s look at an example:
- A defined critical operation for insurers is claims processing.
- A defined material service arrangement is claims management.
The critical operation would capture the end-to-end process, from the customer first initiating their claim, to receiving their payout or having their claim declined. Parts of that process could be outsourced – perhaps the initial triaging by a call centre, the work conducted by assessors, or outsourcing of the final transaction processing. Each of these are part of claims management, so each of those providers would be a material service provider.
It’s worth noting that the definition of material arrangement includes those that expose the organisation to material operational risk, not only those that map directly to a critical operation. For example, all entities must consider outsourced risk management and internal audit activities as material.
For non-APR-regulated entities, how do you view other regulators’ attitudes towards the requirements of CPS 230?
In our view, CPS 230 is simply a good operational risk management standard that could be applied to any sector or organisation (tailored based on size and complexity as needed). While this is our opinion only, I expect that other regulators will consider the requirements of the standard – and the outcomes once it comes into force – when regulating their own sectors. While they of course can’t enforce it directly, it wouldn’t surprise if other regulators pointed to elements of the standard as recommended practice.
To throw out a personal opinion, I wonder whether the Critical Infrastructure Risk Management Plan Rules from the Cyber and Infrastructure Security Centre might have aligned more closely to CPS 230 if timing had been slightly different. In my view, applying the requirements of CPS 230 – especially the process mapping, controls assurance and material service provider management – will improve the resilience of our critical infrastructure providers.
We use the risk management and vendor management modules in Protecht. Does the operational resilience module integrate with these to ensure data is not duplicated?
The Operational Resilience module has been designed to integrate with risk and control taxonomies, business units and users to support aggregation of data and insight across the organisation. Minor configuration may be required to integrate – for example, if you have an existing Resources register it may need to be modified to work in the module, to ensure that key information such as vulnerability, criticality and Recovery Time Objectives data is captured.
Protecht's vendor risk management solution has been designed to integrate with the operational resilience module, making it easier to understand where vendor-managed resources are part of your critical operations.
Next steps for your organisation
A complete enterprise risk management approach, supported by appropriate systems and tools can enable:
- Process mapping an end-to-end view of your critical operations and the information assets that support them, including those owned by third parties
- A vendor risk management program that enables ongoing monitoring and assessment of your third parties, including controls assurance
- An ISMS that enables comprehensive control testing and assurance
- Incident response playbooks linked to plausible scenarios and critical operations
You can find out more about how to build and manage the systems and programs laid out above in our free eBooks covering operational resilience, vendor risk management, IT risk management and cyber risk management.
If you missed the live CPS 230 webinar, you can watch it on demand here:

