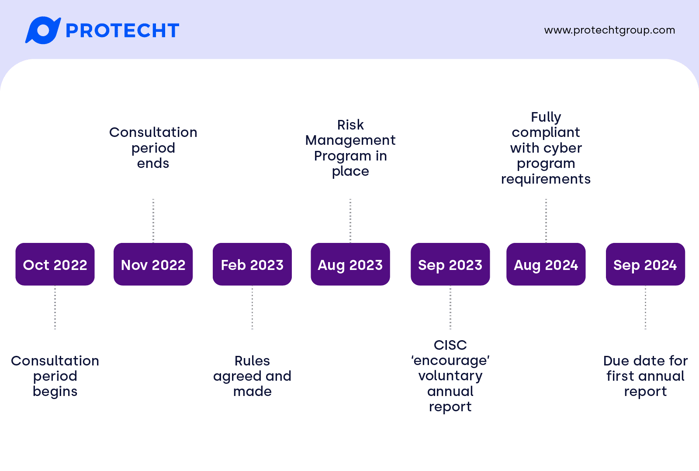
The countdown has begun for Australian critical infrastructure asset operators to have their risk management program in place. The rules commenced on 17 February 2023, and entities will need to be compliant by 17 August 2023. The changes from the consultation draft issued in October 2022 are minimal.
In this blog we cover:
- Timelines for implementation
- Differences between proposed rules and final rules
- Integrating the rules into an ERM and operational resilience framework
- Thoughts on ownership
Relevant timelines
The Minister for Home Affairs signed the Security of Critical Infrastructure (Critical Infrastructure Risk Management Program) Rules to come into immediate effect on 17 February 2023.
The rules provide a six-month grace period, which means that the covered entities need to have their risk management program in place by 17 August 2023. While the Cyber & Infrastructure Security Centre (CISC) have been open that this does not mean that all treatments need to have been fully implemented, they are expecting progress.
There is an additional 12-month grace period on meeting the cyber requirements of the rules, which require meeting one of the five outlined frameworks in the rules or an equivalent standard.
Differences between draft and final rules
While there are differences between the exposure draft and the final rules, most are minor changes in language or definitions or reference to other laws rather than material change. The acronym CIRMP has been formally introduced (which doesn’t exactly roll off the tongue). A few minor modifications that are noteworthy:
- References to ‘critical sites’ have been replaced with ‘critical components’ (which is defined in the SOCI Act)
- Under personnel hazards, the requirement to assess critical workers ‘on an ongoing basis’ has been removed (a source of questions during consultation)
- Change from ‘high risk vendor’ to ‘major supplier’. While underlying definitions did not change in the rules, it has made supporting guidance clearer
- ‘Natural hazard’ and ‘supply chain hazard’ now have specific definitions. Natural hazard lists examples (from fire to pandemic), and most noteworthy about the supply chain definition is the mention of over-reliance on particular suppliers.
An aside on material risk
Another noteworthy exclusion is one of the definitions for material risk from the exposure draft of the Rules: “An impairment of the asset that may prejudice the social or economic stability of Australia or its people, the defence of Australia or national security”. This has been removed, moving reliance to the next subsection which remains intact: “a stoppage or major slowdown of the CI asset’s function for an unmanageable period”.
While the removed definition might have been somewhat subjective (though if I’m being picky on the retained clause, unmanageable period for whom?), it was one of the few definitions which linked directly to external impact. The related SOCI Act definition of ‘relevant impact’ relate primarily to the availability, integrity, reliability and confidentiality of the asset – not the actual impact it has on stakeholders or community.
You can make a reasonable argument that if an asset is already on the government critical infrastructure register, this link has already been made, and CISC communication during consultation has certainly been outcome focused. My point and recommendation here is that you when you build your risk management program (or adapt an existing one), don’t make the asset the focal point; consider the ultimate impact on your stakeholders.
Integrating the rules into an ERM and operational resilience framework
Here is a quick overview of integrating the rules into your existing programs – or to get you started if you need to kickstart one.
Understand your critical asset
That seems like a straightforward statement. Before simply listing all your critical components, consider the processes that help you deliver a service or output to your customer. As noted earlier, it isn’t the unavailability of the asset that matters, it is the failure to deliver a service to your stakeholders.
Once you’ve understood the processes, you can identify resources that support those processes. Those resources might be critical components, but they might also be critical workers that need to operate those critical components. At this point you should also distinguish between resources you own and those owned by third parties.
Visual mapping helps immensely with communicating how these processes and resources fit together.
Identify risks and scenarios
Consider potential risks and scenarios that might affect one or more resources. This might help you avoid single points of failure, or scenarios where redundancies that you have in place would be rendered ineffective, and where additional controls or other action is required.
Leverage existing risk taxonomies across causes, risks or impacts that may already be part of your risk framework. If you don’t currently separate risks from their causes, we recommend looking at our Risk Bow Tie eBook or online training module to help analyse your risks. This exercise often simplifies risk libraries and help you focus on what really matters.
Document your control framework
If you don’t already, identify and document the controls that you already have in place. Ideally this should include the objective of the control (how it is intended to modify risk), how it operates, how it is tested, and whether it is subject to independent assurance.
You can find out more about optimising your controls in our eBook on controls.
Identify treatments
Once you’ve understood your assets, risks and controls, you can evaluate whether the residual risk is something you are willing to accept. If not, you may need to implement new controls, or re-engineer processes to eliminate the risk.
These should be documented with clear accountability and commitment of resources (personnel or financial) to implement within a defined deadline.
Thoughts on ownership
A challenge we find that some of our customers face when integrating their risk management into their day-to-day operations is who owns what.
Under the rules, a named person(s) has to be responsible for developing and implement the risk management program, or for keeping it up to date. While someone might be required to have oversight for the program as a whole and maintain a bird’s-eye view, it is likely more practical to push ownership of particular elements further into the organisation.
You may already follow a risk governance model such as the Three Lines Model, but you may want to consider:
- Whether there is a designated owner for each critical component (responsible for its performance and receiving assurance about linked controls)
- Who will be involved in risk workshops or other risk identification activities (subject matters experts are likely much better at identifying specific risks and causes)
- Who is responsible for running those workshops
- Whether there is a designated owner for each identified control (if there isn’t, who is accountable for making sure it continues to operate?)
- Whether someone other than a control operator should be providing independent testing or assurance
- Who is responsible for tracking key risk indicators and key control indicators
- Who is responsible for collating risk data and reporting on an ongoing basis – and who they report to
While the person responsible for oversight may drive some of these activities, if roles and responsibilities in your framework are not clear, risks may not be as well managed in reality as they appear on your risk management program.
Closing thoughts and next steps
CISC have been clear during consultation that they are more interested in outcomes than compliance. That means investing in the tools that can enable good risk insights – and direct decision making to mitigate the material risks.
Protecht recently launched the Protecht ERM Operational Resilience module, which helps you identify and manage potential disruption so you can provide the critical services your customers and community rely on.
Find out more about operational resilience and how Protecht ERM can help:
