Cyber risk clarity. Confidence where it matters most.
Protecht’s AI-enabled cyber and IT risk solution helps cyber security, technology and risk leaders cut exposure, strengthen posture, and prove compliance. By unifying risks, assets, incidents, and controls in a dedicated workspace, you can reduce duplication, accelerate responses, and streamline compliance.
Know your true risk posture.
Get a unified view of cyber posture across risks, assets, incidents, vulnerabilities, and controls, with compliance mapped in from the start
-
Dashboards spanning risks, incidents, vulnerabilities, and compliance requirements
-
Control framework alignment and cross-mapping to reduce duplication (NIST CSF, Essential Eight)
Give the board confidence, not complexity.
Translate cyber posture, compliance progress, and control maturity into clear business terms that executives can act on.
-
Executive dashboards with posture, incidents, trends and compliance KPIs
-
AI-powered insights for reports aligned to governance cadence
-
Compliance and audit reporting supported by centralised evidence and audit trails
Turn incidents into continuous assurance.
Make every incident a source of compliance and assurance evidence while strengthening resilience
-
AI-powered incident capture, review, closure, and lessons-learned workflows
-
Configurable escalation workflows and SLAs
-
Incidents linked to risks, assets, controls, and compliance standards for traceability
Prioritise assets that matter most.
Focus protection and compliance assurance on the assets that carry the most business and regulatory risk.
-
Asset registers capturing criticality, owner, and related controls
-
Vulnerability and issues data linked to assets
-
Evidence-based asset risk ratings
Protecht cyber and IT risk solution brochure.
Reduce duplication, accelerate responses, and streamline compliance by unifying risks, assets, incidents, and controls in a dedicated workspace.
IT risk management eBook.
What IT risk is, why it matters, why it’s different from cyber risk, and why it’s not just a concern for the IT department.
Safer, smarter cyber risk with Protecht.
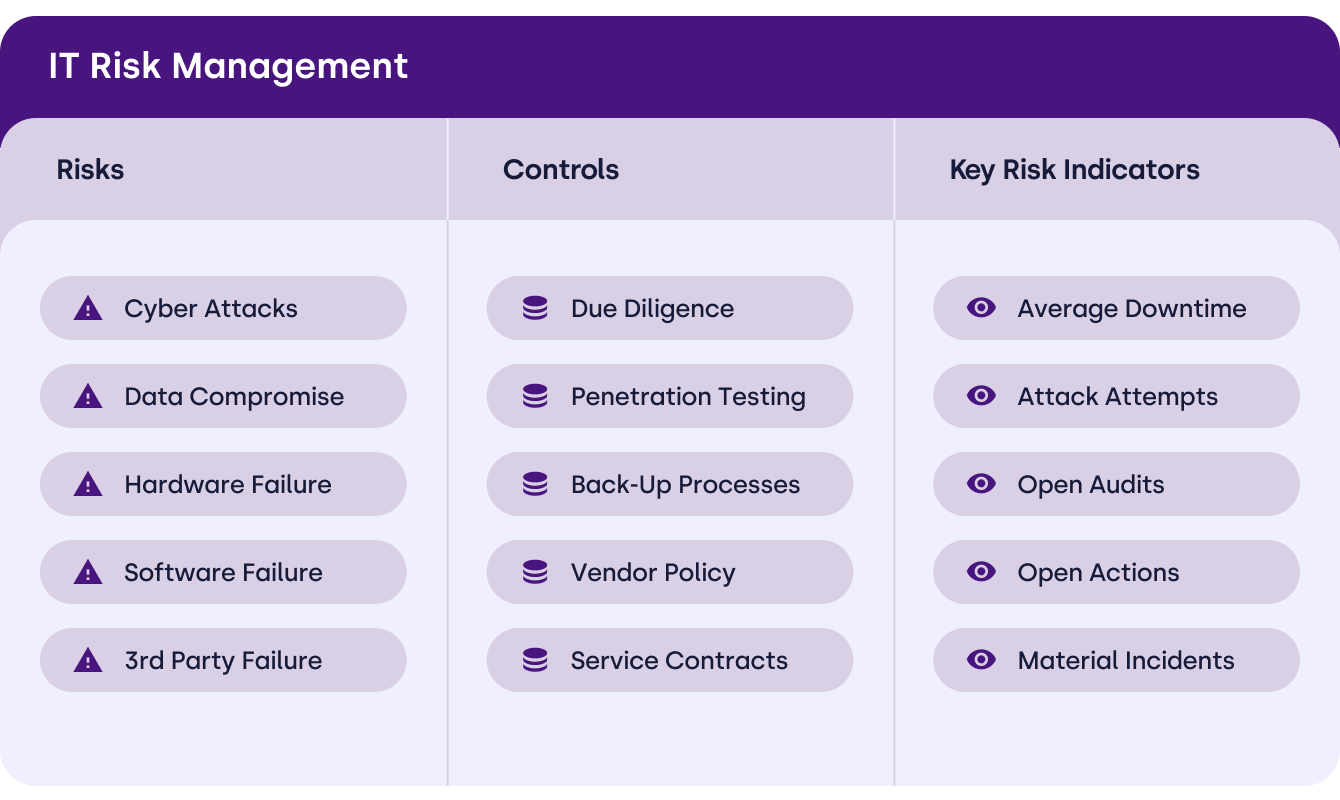
Workspace tasks
Stay in control of every cyber action across the organisation. Quickly view, prioritise, and complete tasks across your cyber risk lifecycle with clear visual indicators for overdue and upcoming work.
- Immediate visibility of overdue, due, and open tasks to prioritise action
- Fast access to key frameworks and obligations for audit and compliance tracking
- Assign ownership, monitor progress, and escalate automatically to stay audit-ready
Workspace metrics
Track performance and progress at a glance. Real-time metrics show how cyber risk management activities are progressing, helping leaders focus effort where it matters most.
- Posture and performance indicators across risk, incident, and control workflows
- Trend views highlighting overdue reviews, gaps, and assurance status
- Framework-based metrics to demonstrate maturity and alignment with standards
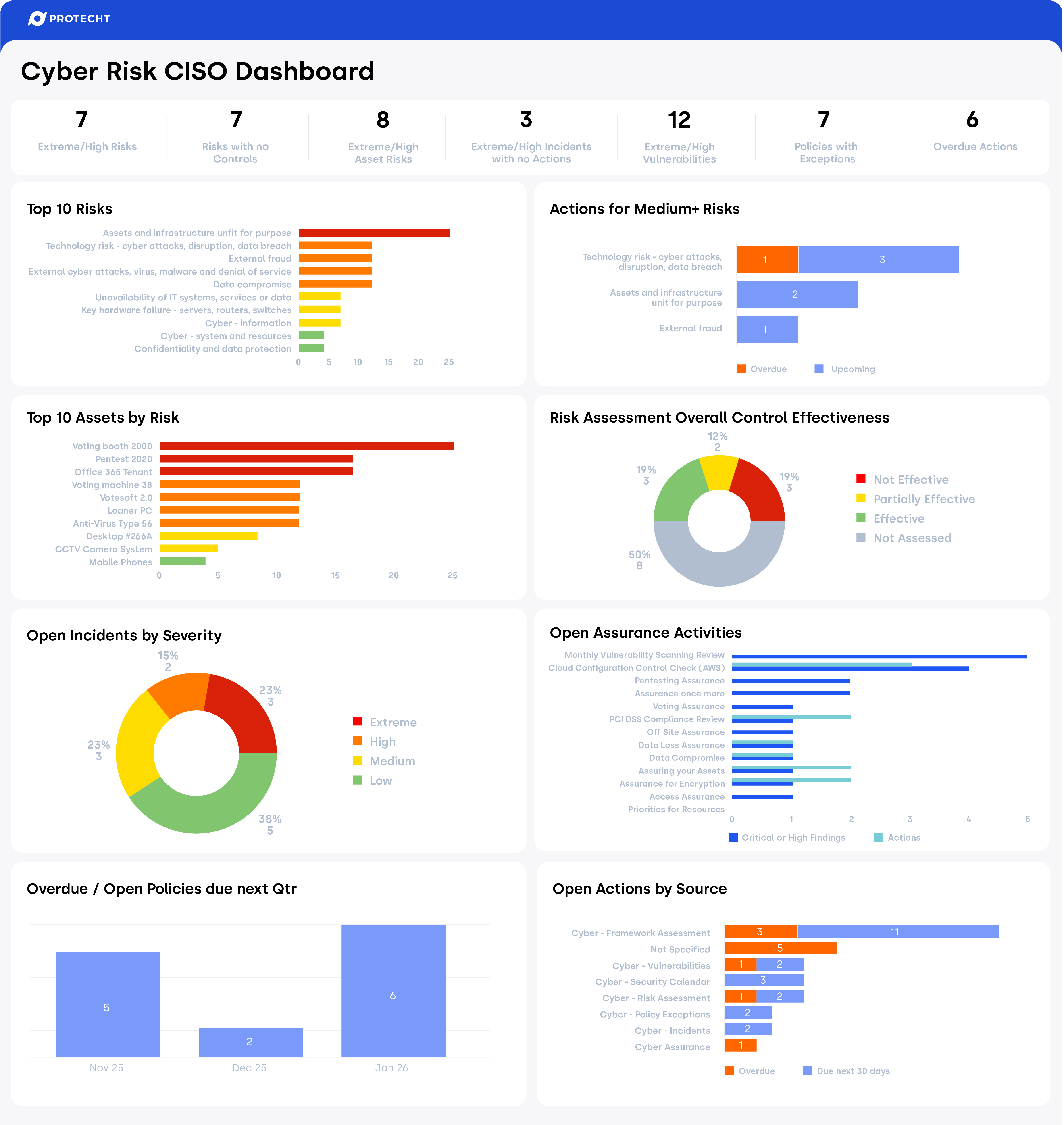
Dashboards
Communicate cyber posture with clarity and confidence. Prebuilt, executive-ready dashboards translate complex cyber data into clear, actionable insights for internal and external stakeholders.
- Out-of-the-box analytics across incidents, vulnerabilities, assets, and risks
- Clear reporting on control maturity, assurance coverage, and gaps
- Demonstrate resilience and compliance to executives, auditors, and regulators
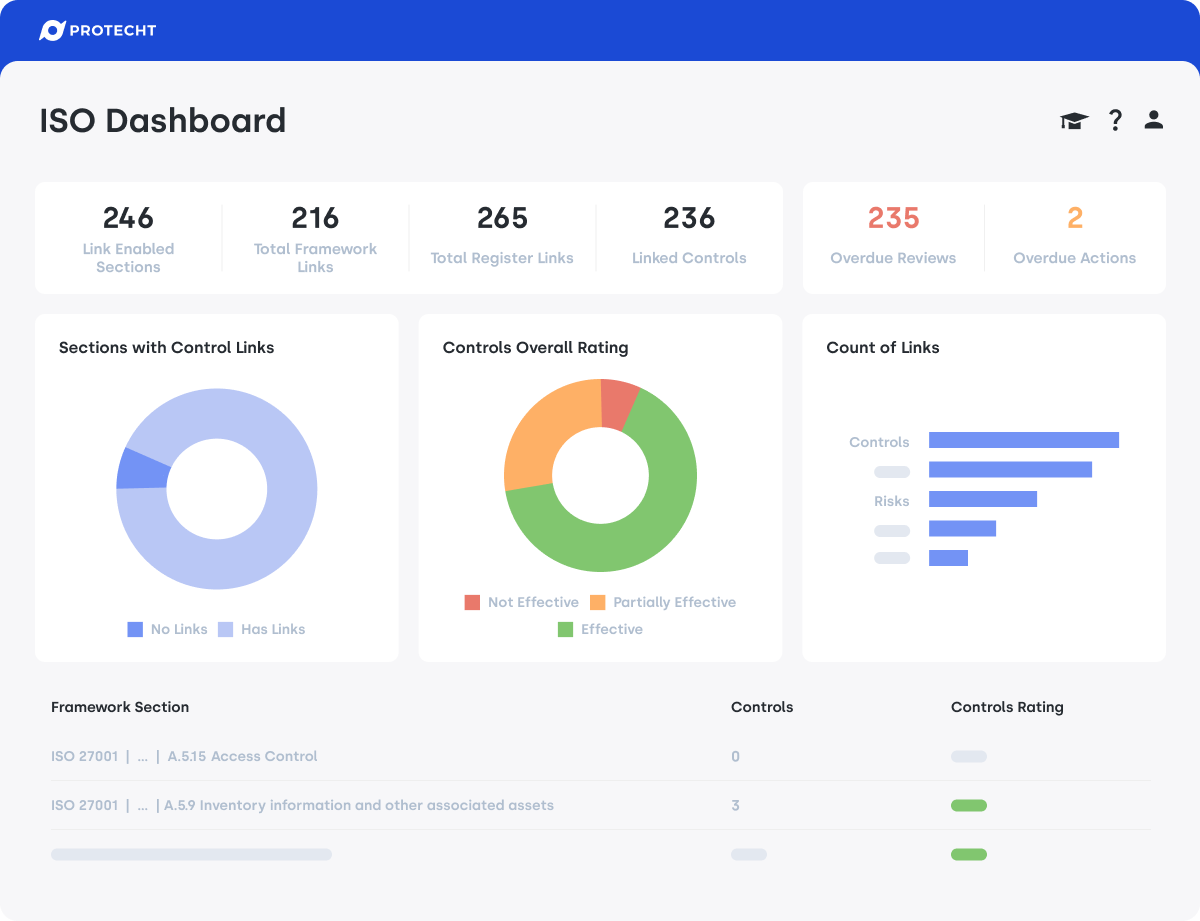
Cyber registers
Structure and consistency for every cyber activity. Purpose-built registers capture, track, and link data across your cyber ecosystem, from assets to incidents and controls.
- Registers for risks, threats, vulnerabilities, assets, incidents, and assurance
- Linked workflows to drive remediation, testing, and evidence collection
- Complete audit trails for every action and review cycle
Cyber analytics
Turn data into actionable insights. Ready-to-use analytics and reports help you monitor posture, identify trends, and prioritise improvements.
- Dashboards for incidents, vulnerabilities, assets, policies, and assurance
- Deep-dive reports for frameworks such as ISO 27001, NIST CSF, and SOC 2
- Real-time visibility of cyber maturity, exposure, and progress over time
Cyber frameworks
Confidence through alignment with global standards. Accelerate compliance and reduce duplication with mapped frameworks and controls out of the box.
- Integrated libraries for NIST CSF, SOC 2, CPS 234, Essential 8, PCI DSS v4.0.1, and more
- Cross-mapped control structures for streamlined evidence collection
- Support for emerging standards including NIST AI RMF, ISO 42001, and VAISS-AU
Preconfigured content – for a turnkey launch.
Optimise your risk management at the click of a button. Set up and maintain your ERM system with Marketplace: preconfigured registers, dashboards and reports.
Explore some of the assets that are included within our cyber offering:
Cyber risk assessment and management
Identify, assess, and manage cybersecurity risks across your organisation’s critical assets, operations, and objectives. The Cyber Risk Assessment register and dashboard help you:
-
Capture and evaluate cyber risks in a centralised register
-
Prioritise risks by likelihood, impact, and business context
-
Link risks to relevant controls, incidents, and treatments to track exposure and response
Cyber threats and vulnerabilities
Proactively monitor and address emerging threats and weaknesses before they escalate. The Cyber Threats and Cyber Vulnerabilities registers and dashboards help you:
-
Maintain visibility of known and emerging threats
-
Track vulnerabilities by system, owner, and severity for prioritised remediation
-
Map vulnerabilities to risks, assets, and controls for effective risk-based management
Cyber assets and asset assessments
Keep an up-to-date inventory of your critical information assets — from systems and applications to data and infrastructure. The Cyber Assets register and Cyber Asset Assessment report help you:
-
Document ownership, classification, and criticality of each asset
-
Link assets to related controls, risks, and incidents
-
Support risk-based asset protection and compliance alignment
Cyber incidents and issues management
Ensure every incident becomes an opportunity to strengthen resilience. The Cyber Incidents and Cyber Issues registers and dashboards help you:
-
Log, classify, and manage incidents from identification to closure
-
Track trends, root causes, and lessons learned to prevent recurrence
-
Link incidents to impacted assets, controls, and treatments for full traceability
Controls assurance and testing
Demonstrate control effectiveness and maintain continuous assurance. The Controls Assurance and Controls Testing registers and dashboards help you:
-
Map and test controls across frameworks such as NIST CSF, SOC 2, and CPS 234
-
Automate test scheduling, record results, and monitor exceptions
-
Provide a defensible audit trail for regulators and certification bodies
Framework assessment and alignment
Evaluate your cybersecurity posture against leading global standards. The Framework Assessment register and Framework Gap Report help you:
-
Compare your implementation against frameworks including NIST CSF
-
Identify control gaps and prioritise remediation activities
-
Align your cyber strategy with organisational risk appetite and regulatory obligations
Cyber policies and documents
Centralise and govern your cybersecurity policies and key documentation. The Cyber Policies and Documents register and dashboard help you:
-
Maintain version-controlled records of all policies, procedures, and standards
-
Track review dates, ownership, and policy exceptions
-
Surface outdated or missing documents to ensure audit readiness
Cyber actions management
Keep control of all cyber-related actions across the business. The Cyber Actions register and dashboard help you:
-
Create, assign, and track actions from incidents, risks, and audits
-
Monitor progress by owner, priority, and due date
-
Identify and escalate overdue actions to maintain accountability
Cyber assurance and audit readiness
Provide ongoing visibility of assurance activities and audit outcomes. The Cyber Assurance register and dashboard help you:
-
Record audit findings, recommendations, and remediation steps
-
Monitor progress across all assurance cycles
-
Demonstrate continuous improvement and compliance maturity to executives and regulators
Cyber security calendar
Plan and execute key cybersecurity activities with confidence. The Cyber Security Calendar register and dashboard help you:
-
Schedule and monitor audits, reviews, training, and maintenance tasks
-
Gain visibility of upcoming deadlines and ownership
-
Ensure critical security operations are performed on time and aligned with governance cycles
Find out more about cyber and IT risk management.
Thought leadership and product demonstration webinars
Thought leadership webinar
Cyber risk: Get on top of your controls and frameworks.
Product demonstration webinar
Streamline your IT controls: Simplify cyber compliance with Protecht ERM.
Thought leadership webinar
Speaking the same language: Bringing IT and cyber risk to your enterprise view.
News and commentary
Related industries
Find out how Protecht’s industry expertise can help your IT risk management teams meet their business requirements across our key industry verticals:
-
Banking
Manage risk and compliance with a platform configured to empower banks and credit unions.
-
Insurance
Stay on top of regulatory requirements with real-time reporting that gives every user risk ownership.
-
Fintech
Manage risk and compliance with a platform designed for rapid growth in a rapidly changing environment.
-
Education
Manage risk with a platform configured to support staff, students and your business needs.
-
Government
Manage risk and compliance with a platform configured to meet the needs of government entities.
-
Aged care
Manage risk and compliance with a platform designed to enhance safety and accountability in aged care.






