For most organisations, vendors are the most significant third party and – as a result – are the major source of third-party risk. As a result, it makes sense to focus on vendors and the management of the various risks they pose.
Our Vendor Risk Management webinar in May 2023 gave an overview of vendor risk management’s drivers and benefits, and set out how you should go about implementing your organisation’s VRM program.
In this blog, we'll discuss the audience polls and the questions asked at the webinar.
Poll results
Results for our surveys were quite consistent across regions, so the data has been presented together.
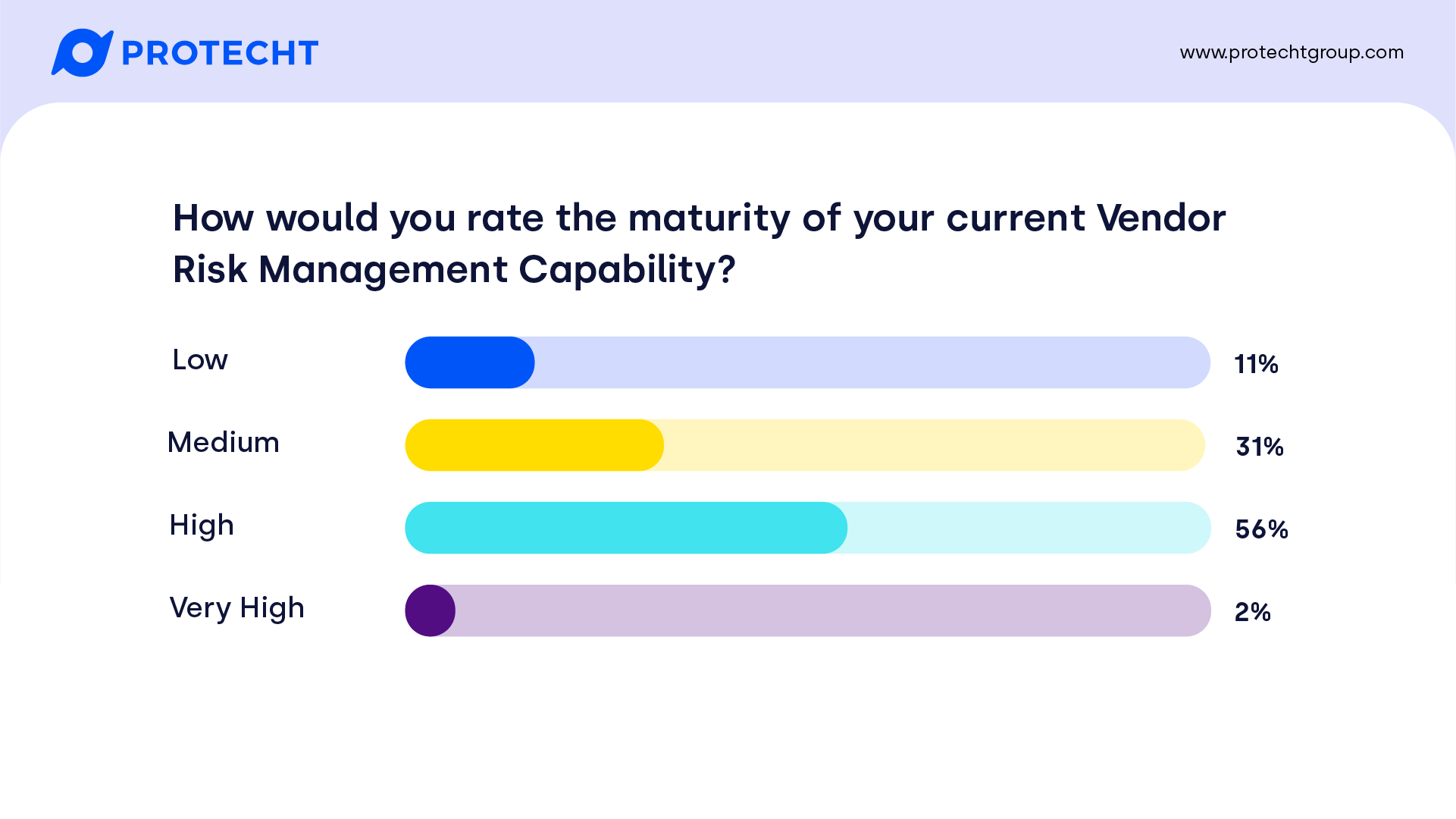
While we expected most to be around the middle, there are still close to one-third who consider their maturity to be low. While we didn’t ask participants the size of their organisation, we expect that the larger the organisation, the more likely they are to be in the higher tiers. Given some of the inherent challenges in managing the extended enterprise, an assessment of very high is difficult to achieve – congratulations to the few of you who have achieved it!
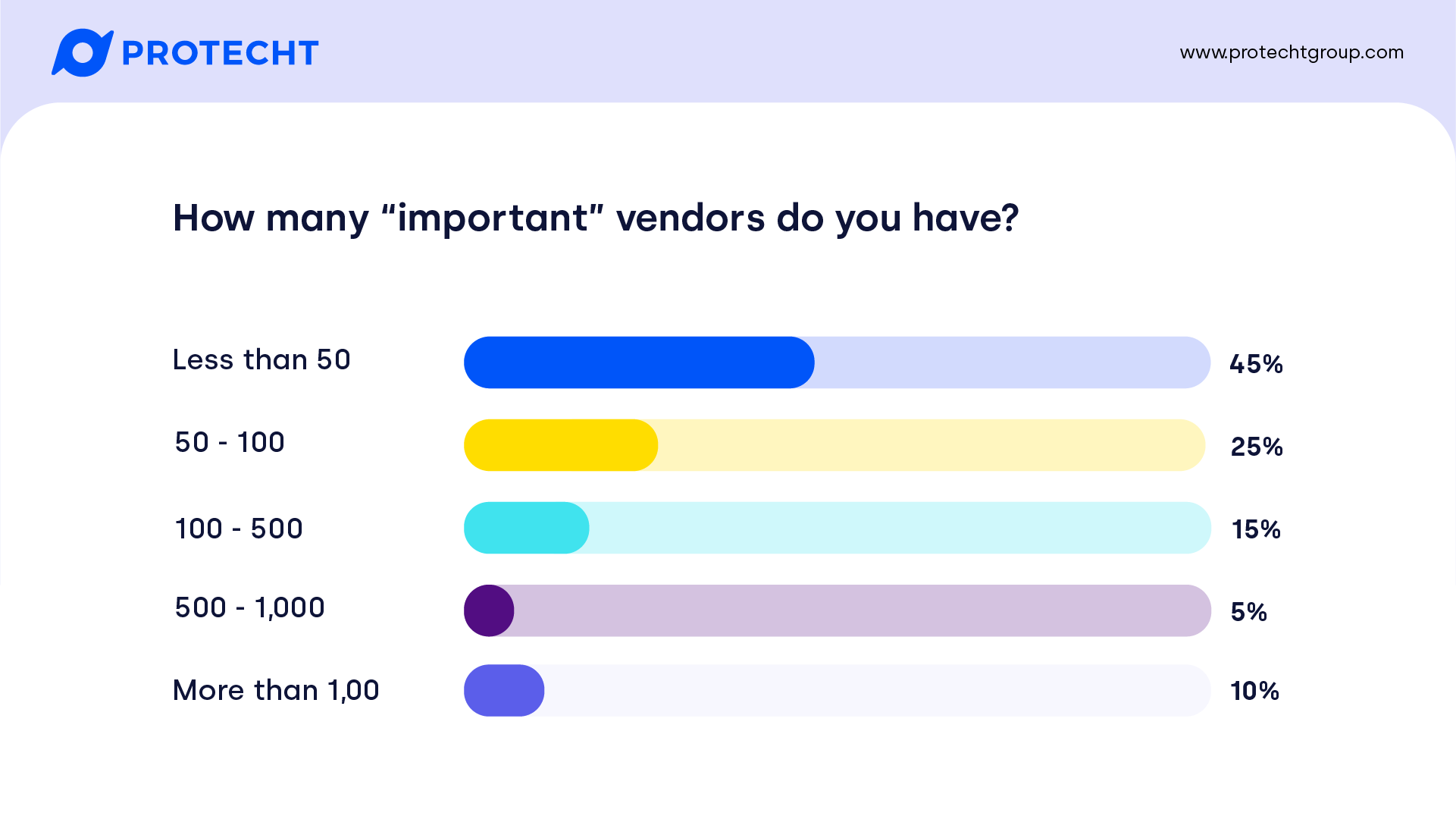
Notwithstanding “Important vendors” has a degree of implicit subjectivity, over half have more than 50 important vendors with 10% having over 1,000. It does highlight the extent of the extended enterprise and vendor ecosystem remembering that this does not cover the 4th and 5th + parties!
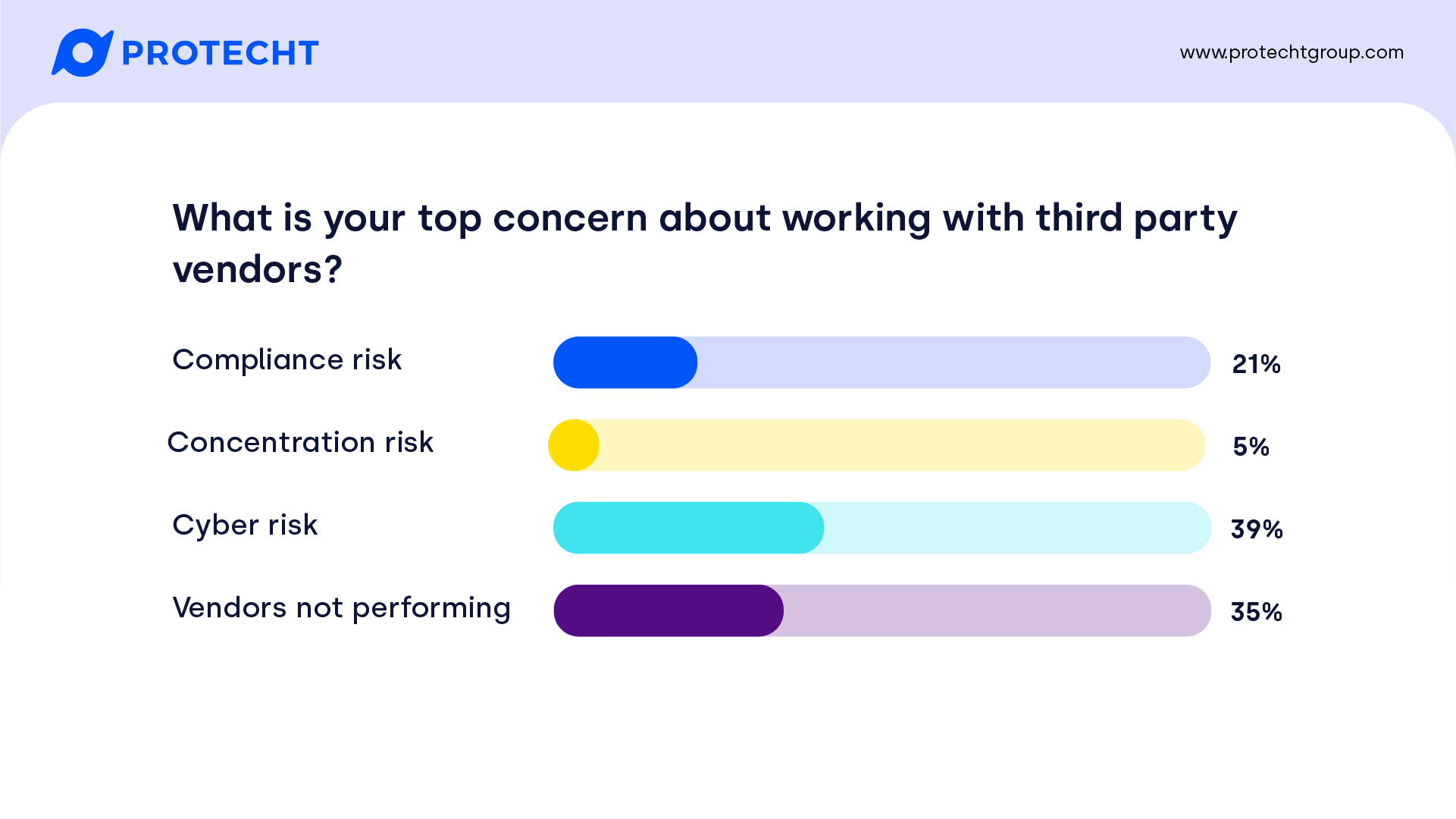
Fairly consistent globally, with cyber rising to the top, followed by vendors failing, though EMEA had a slightly higher focus on vendors failing. The focus on cyber is not surprising given the consistent news stories of high-profile breaches in all regions, particularly those caused by third parties or digital supply chain attacks.
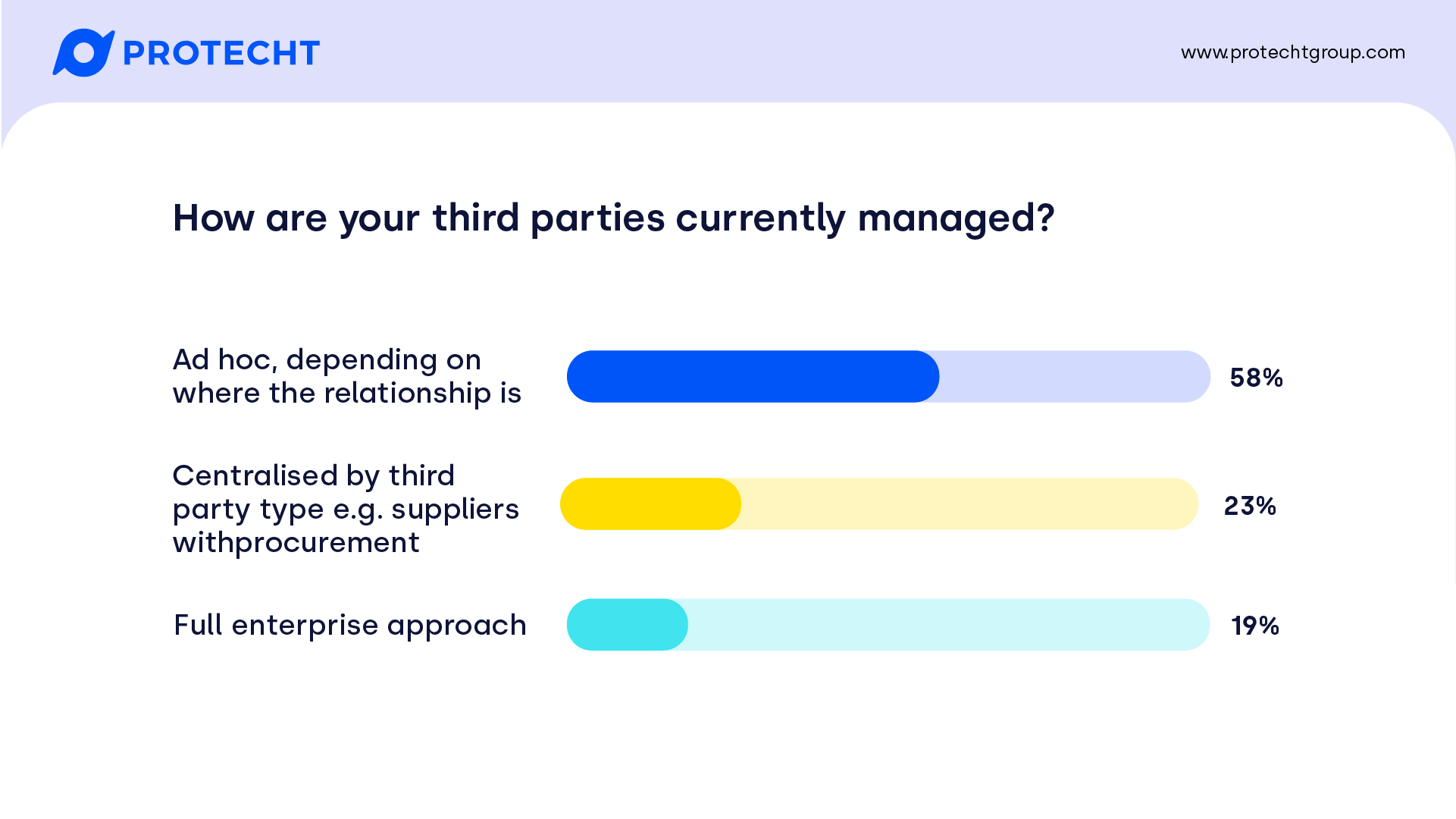
Great to see that close to 1 in 5 took an enterprise approach. Centralising by third party type moves to some form of standardisation, but may still result in a siloed approach and inability to consider risks across the entire organisation. With many still managing third parties in an ad hoc manner, there is a lot of room for digitisation and automation.
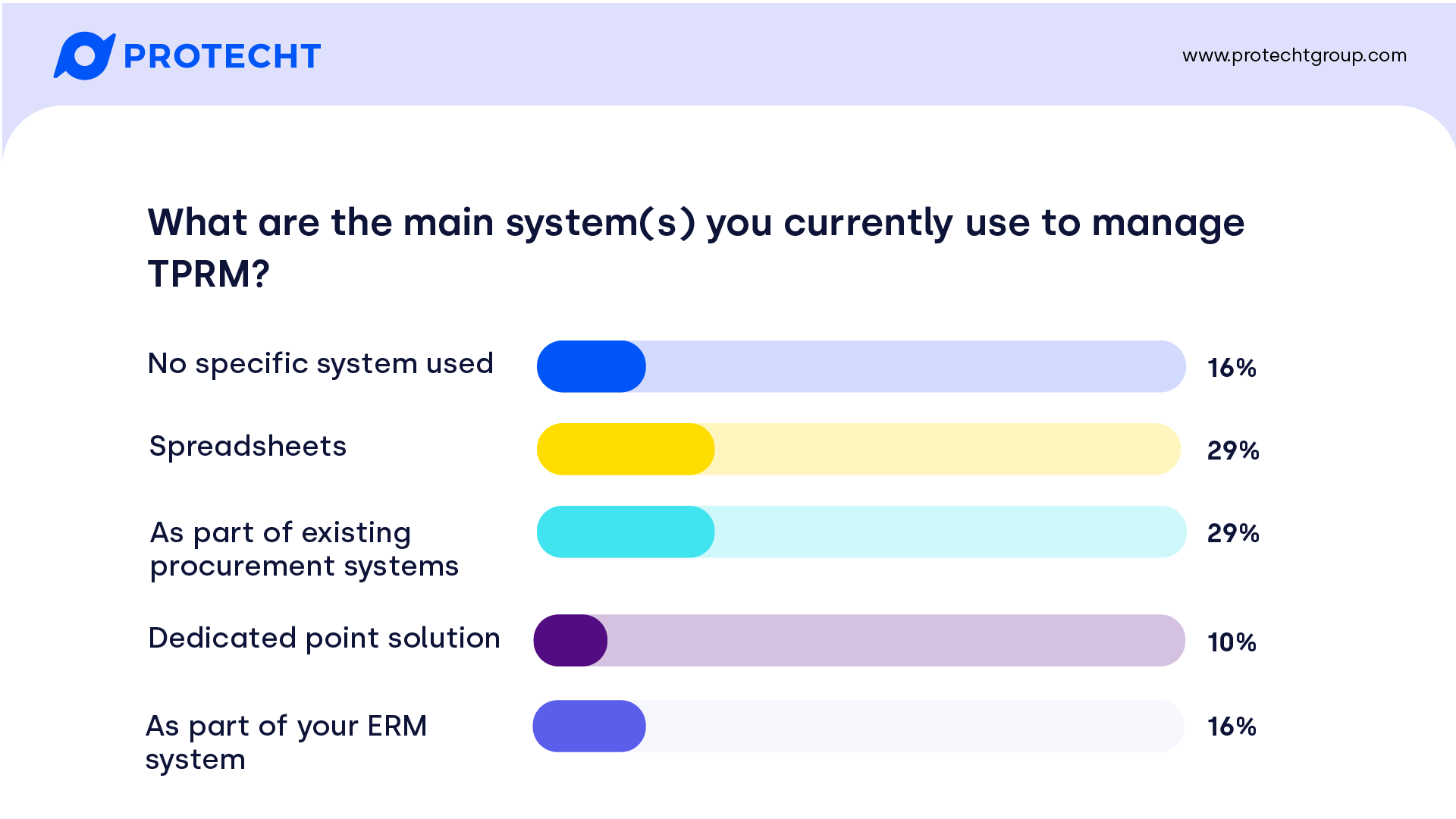
Spreadsheets are ubiquitous as expected in a discipline that is in its infancy, take equal top slot with procurement systems giving them a run for their money. What’s pleasing to see is that more people are integrating their vendor risk management into their ERM framework rather than relying on a point solution, the best and most efficient way to go in our opinion!
Questions
Q1: When it comes to systemic concentration risk, is there any comfort to be gained from being in the same boat as all of your market peers?
Q2: Define the tier of a vendor / how do you complete an inherent risk assessment?
Q3: How often should contingency plans covering long term strategic objectives be reviewed?
Q4: What advice do you have for clients who can end up stuck in a never-ending due diligence process after gaps are identified with vendors?
Q5: Would you consider separate business units within the same large organisation as 'vendor risks'?
Q6: What are the 'best' ways to manage a vendor on an ongoing basis?
Q7: How do you manage being highly dependent on a single vendor, especially for major vendors like SAP/Oracle?
Q8: Within the business, which function should manage and own vendors? Where does vendor risk stand in terms of the Lines of Defence model?
Q9: Do you have a view on how to look further through the supply chain into fifth/sixth parties and obtain a proportionate view on assurance undertaken on these parties?
Q10: How do you capture and measure residual risk?
Q1: When it comes to systemic concentration risk, is there any comfort to be gained from being in the same boat as all of your market peers?
I would err on the side of no, or at least not something you should rely on. Particularly if you are regulated, you may have a minimum level of service that is expected of you, regardless of the source of disruption or incident.
While some issues may require a broader industry response, often it is those most prepared that come out ahead. Consider whether you might be able to develop contingencies for vendors that are systemically important, such as having alternative suppliers on standby or introducing alternative methods to deliver the same outcomes to customers.
Q2: Define the tier of a vendor / how do you complete an inherent risk assessment?
The tier of a vendor is comparable to an inherent risk assessment, and is the outcome of an initial triage process. Different frameworks and contexts may differ, but some common factors for this initial tiering include:
- Financial – What is the value of the engagement? Higher value engagements typically require more due diligence given the higher costs if they fail. This should never be the only factor – some vendors may provide services for free for other advantages, such as access to your customer base or confidential information.
- Strategic importance – How important is this vendor to achieving your strategy? Some vendors may supply a service that can be easily replaced, while others may require a change to strategy if they fail or walk away.
- Information security – Will the vendor have access to our customer data, or have access to our systems? What type and extent of access will they have?
- Business continuity – How will our own operations be disrupted if the vendor is disrupted or fails?
- Reputation – If this vendor were to fail or suffer a reputational issue, how likely is it that we would also be affected by association?
- Compliance – Does this vendor assist us with meeting our compliance obligations? If yes, what is the importance of those obligations?
This initial tiering then provides an assessment of the risks inherent in the relationship with the vendor, which can then drive due diligence that is tailored, rather than a bloated one-size-fits-all approach, and determine the level of ongoing monitoring that is required for assurance.
Q3: How often should contingency plans covering long term strategic objectives be reviewed?
This will be contextual and depend on the rigour required for your contingency plan (the level of detail and frequency may be dictated in some regulated sectors). The short answer is – as frequently as needed to have reasonable assurance that it remains effective.
We would suggest at a minimum conducting a desktop walkthrough with key stakeholders on an annual basis. When setting your contingency plans, you may want to identify key risk indicators or implement horizon scanning that might identify changes to the environment that might render the contingency plan ineffective, so that it can be proactively reviewed.
Q4: What advice do you have for clients who can end up stuck in a never-ending due diligence process after gaps are identified with vendors?
Automation of those follow-ups and having systems that are transparent about what is outstanding certainly help. If the vendor still isn’t providing the information, you need to identify why. It may also depend on where in the process these gaps are identified. If they haven’t been onboarded, you might be able to progress an alternative provider who can provide you the assurance you require.
If they are already onboarded, this can be trickier to solve. Ideally, there would be contractual clauses related to that lack of due diligence you could rely on – though once you rely on a contract, it can also affect the relationship with the vendor. If you don’t already, consider whether new contracts you negotiate include penalties or some other consequence if required due diligence is not provided by a certain due date if you can’t wait for it to be assessed before a vendor is onboarded.
You might also consider whether the risk is actually acceptable without the actual due diligence. If they don’t provide it, are you going to terminate the agreement? If not, consider whether there is any value in continuing to ask for it.
Q5: Would you consider separate business units within the same large organisation as 'vendor risks'?
Your organisation (and all its business units) would usually be the first party, with your customers being the second party. As your business units are part of your organisation, you normally wouldn’t need to assess them as vendors. You often have more direct access to the information that you would ask an external vendor to provide.
However, it can be applied if relevant to larger organisations. In particular, larger organisations or groups may be multiple corporate entities, where one entity provides services to another in the group. In some sectors (particularly financial services), there may be regulatory requirements for related entities to have formal contracts or service agreements in place.
If you are not regulated in this way, we suggest you rely on the adage, “fit for purpose”. The main reason for following a vendor risk management process is to gain assurance that risks arising from relationships outside your direct influence are being effectively managed. If you apply a vendor risk management process, ensure it isn’t duplicative of other risk management processes.
Q6: What are the 'best' ways to manage a vendor on an ongoing basis?
Ideally it is based on strong personal relationships with the vendor. Combining both relationship management and vendor risk management processes together, here are some high level tips:
- Set the expectation for ongoing monitoring with key stakeholders at the vendor. In particular outline why that ongoing monitoring is in place; it might help the vendor proactively offer important information you don’t ask for
- Automate as much as possible to make the process easy for both you and the vendor, and provide transparency on any actions that are outstanding. Focus on the outcome of assurance, not the process of data collection
- Automation and linking to your Enterprise Risk Management system can also identify particular triggers (such as Key Risk Indicators moving out of tolerance) for updating risk assessments or other due diligence, helping you move from doing them at a defined frequency to a more proactive risk-based approach
- If you have regular relationship management meetings, include risk management or due diligence as part of that agenda. Have a standing question about whether anything has changed at the vendor or your own internal processes that might warrant a review of any existing risk assessments or due diligence
- Be transparent about what you are asking for, why, and what you intend to do with the information you request
Q7: How do you manage being highly dependent on a single vendor, especially for major vendors like SAP/Oracle?
Being highly dependent on a single vendor is likely to link into your business continuity or operational resilience processes. Usually you want a higher level of assurance that the vendor will be able to deliver their services, which might include an assessment of the vendors own business continuity arrangements. For high impact vendors, you might also collaborate with them on how incidents will be managed. Regardless of the level of assurance you receive, you will likely also want your own internal business continuity plans to include a scenario where they fail.
If you have multiple vendors that provide a similar or alternative service, the reliance on any one of them, and therefore the required assurance, diminishes. This can be established during your triage process, which should then influence lower ongoing due diligence, enabling a risk-based approach. For example, for critical providers you may do deep dives into their information security frameworks, where for less critical providers you may simply request their most recent certification.
Q8: Within the business, which function should manage and own vendors? Where does vendor risk stand in terms of the Lines of Defence model?
There isn’t a single right answer, but let’s break down the question into who owns vendors, and who owns the vendor risk management framework.
Each vendor will have a different owner, which ideally will be management in the First Line. They are responsible for the objectives which the relationship is intended to support, and should therefore own the risks and performing the due diligence.
Second Line risk teams may own the vendor risk management framework and related processes, as part of the overall Enterprise Risk Management Framework. For some, it may be owned by procurement or finance. While information security is often a component of a vendor assessment, it is not the only consideration. If it is owned by IT, it may imply a silo approach where non-IT vendors are not part of your vendor framework. If a second line team owns the vendor risk framework, it does not mean they should be conducting due diligence or risk assessments on behalf of vendor relationship owners.
While the above delineation makes sense, we do see a more distributed model in some organisations, particularly larger organisations. For example, if there is sufficient volume there may be specific individuals or teams whose role is to manage certain phases of the onboarding, monitoring and offboarding processes to gain efficiencies in the process. This can also be supported by a range of other roles; information security teams assessing cyber policies and reports, business continuity teams assessing and updating business continuity plans, legal teams assessing contracts, and so on.
You will need to establish the structure that is right for your organisation. You might want to define a desired state, and develop a staged plan on how to reach it.
Q9: Do you have a view on how to look further through the supply chain into fifth/sixth parties and obtain a proportionate view on assurance undertaken on these parties?
There is no easy answer. For your third parties, your due diligence might include assessing their third-party framework. Of course, that only gives you 4th parties. You could assess whether your third party’s framework requires their third parties to also assess their third parties third party framework… I’m already getting cross-eyed.
You may have visibility across your supply chain into who those sub-contractors are without having any direct recourse to gain assurance from them. Depending on the size of vendor / sub-contractor and sector, you may be able to monitor proxies. For example, there are some providers who assess organisations’ cyber or ESG posture based on publicly available information. These could be associated if applicable as metrics with your direct vendor.
A longer-term industry solution is likely to be the increased ratings of parties by specialist independent ratings organisation, based on certain risk types as we currently have for credit risk and cyber risk.
Q10: How do you capture and measure residual risk?
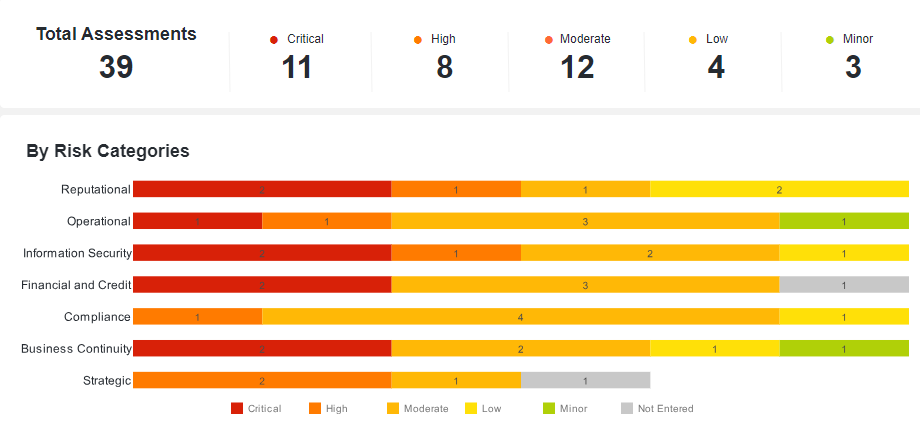
In Protecht’s Vendor Risk Management solution, residual risk can be captured across multiple categories, such as business continuity, information security and compliance, related to the specific exposures of that vendor after you have assessed responses to questionnaires and other due diligence. This provides an aggregated residual risk rating, although we always recommend a ‘sense check’ and allow for manual adjustment of the risk rating.
This allows for an enterprise view of how many vendors relate to specific types of risk, allowing you to not only take a bottom-up approach to managing risks from individual vendors, but also take a top down approach to manage aggregate risk:
Next steps: watch our vendor risk management webinar
Enterprise Risk Management now needs to be Extended Enterprise Risk Management. The days of blaming issues with a third party for your troubles are long gone. The management of your third parties/extended enterprise and the related supply chains is now expected as part of good risk management.
This webinar with Protecht’s Chief Research and Content Officer, David Tattam and Research and Content Lead, Michael Howell, will provide you with an overview of vendor risk management’s drivers and benefits, and set out how you should go about implementing your organisation’s VRM program.

